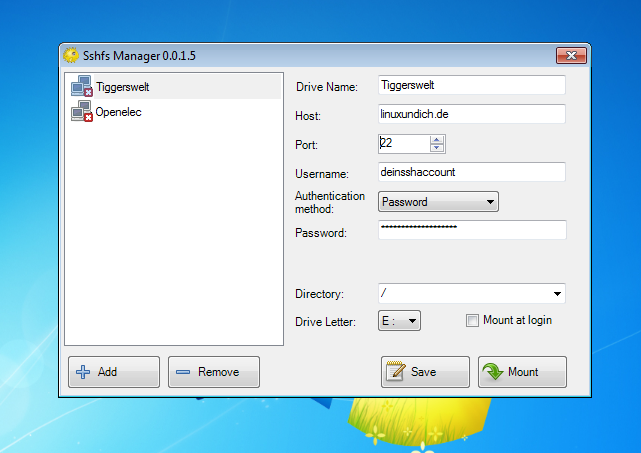
18.5.2 Mapping an IQdesktop container on Windows. Open the Windows Explorer. Right-click on This PC select Map Network Drive and enter the address: sshfs user@127.0.0.1!6900; Note that 127.0.0.1 should be used if you run IQdesktop on your local computer. If you want to access an IQdesktop instance that runs on a server you will need to.
- Sshfs Windows 10 Github
- Sshfs Windows 7
- Sshfs Windows 10 Bash
- Sshfs Windows 8.1 Command
- Sshfs Windows 8.1 App
- Sshfs Windows Server
- Sshfs Windows 8.1 Installer
On older versions of Windows, you may need to run the installer manually. Open the Windows Explorer (right-click on the Windows logo in the bottom left corner), navigate to the Downloads directory (or wherever you saved the installer), and double-click on the file name. A detailed description can be found here. Note, however, that the. This free Telnet and SSH client for Windows can be also downloaded from our PuTTY download page. WinSCP is Also FTP Client. WinSCP is, in addition to being SFTP client and SCP client, also FTP client. It supports also secure variant of FTP, the FTPS. About 4 years Dragging/copying a files on to a sshfs share Windows Explorer window sometimes causes a crash. 1.5.12.8 1.5.12.8.
Wiki > Mounting as a volume
Sshfs Windows 10 Github
It is possible to mount your slot as a remote volume for file management in the same program you use for managing them on your local system. The advantage of this approach over other methods is that your /home folder on the server will be mounted as a local volume or share.
Windows
SSHFS - WinFSP + SSHFS-Win
- Install the latest version of WinFSP
- Install the latest version of SSHFS-Win
- Open Windows Explorer and access
sshfsuser@server.whatbox.caand enter your password when prompted. If this does not work, pressWin+Rand runnet.exe use X: sshfsuser@server.whatbox.cainstead, whereX:is the drive letter you want to use for your slot. You will be prompted for your username and password.
SSHFS - Dokan (alternative)
- Install Dokan Library
- Install win-sshfs.
- Input
server.whatbox.cafor Host,22for the Port,userfor User, select the button next to Password, and input your password. - Change Directory to read
/home/user/and select a drive letter that is not currently used by your computer. - Type in a name for your settings at the top and click Save to use your settings later.
- Click Mount and the drive will appear on your computer. Right-click on the tray icon to disconnect.
Note: Windows 8 or 8.1 will need to run the Dokan library installer in Windows 7 Compatibility mode.
Mac OS X
Finder - FTP with explicit TLS
Sshfs Windows 7
With the Finder focused, open Connect to Server... from the Go menu. Type in ftps://server.whatbox.ca/ and hit Connect. Entering your whatbox username and password will then allow you read-only access to your files through Finder. You will still need to use third-party SFTP/SSHFS software to access/mount your slot as read-write.
SSHFS - Macfusion GUI
- Install FUSE for macOS. Check 'MacFUSE Compatibility Layer' in the installer when installing.
- Download Macfusion and copy it to the /Applications folder
- Connect to your slot via SSH in Terminal to accept the host key.
- Open Macfusion and click on + to add an SSHFS connection
- Input
server.whatbox.caforHost,userforUser Name, input your slot password forPasswordand enter/home/userforPath. - Click on the
Macfusiontab and set a mount point (for example,/Users/OSX-User-Name/whatbox) and a volume name. - Click
OKthen clickMount. If everything went correctly the volume will be visible on either the desktop and/or in the Finder sidebar (make sure to toggle 'Connected Servers' in Finder Preferences)
SSHFS - Command line (alternative)
Install FUSE for macOS and SSHFS for macOS
Open Terminal and create a local mountpoint
mkdir ~/whatboxMount your slot with
sshfs. Once mounted, it will also be accessible in Finder.When you are done, you can use Finder or the
umountcommand to safely eject/unmount sshfs
Linux
Nautilus
From the menu in Nautilus, open Connect to Server... from the File menu. Type in server.whatbox.ca for the Server: and select either FTP (with login) or SSH. Entering your Whatbox username and password will then allow you to manage your files using Nautilus.
SSHFS
- Install FUSE and sshfs through your distribution's package manager. On distributions based on Debian like Ubuntu/Kubuntu, open a terminal window and type
sudo apt-get install sshfs - Add yourself to the fuse user group, if it exists.
sudo gpasswd -a $USER fuse - If you had to re-add yourself to the fuse user group, log out and log back in.
- Create a local mountpoint:
mkdir ~/whatbox - Mount:
sshfs -o idmap=user user@server.whatbox.ca: ~/whatbox - Remote files will now be accessible through a file browser and applications in ~/whatbox
- You're probably going to want this to run every time you boot. You can only do so if you automatically log in via public key authentication. See here or here.Here is an init script for Ubuntu, place it in
/etc/initaswhatbox.conf. Search Google for how to make startup scripts for other distros if your distro doesn't use Upstart.
CurlFtpFS
FTP has often better performance than SSH, so if SSHFS does not work for you, try CurlFtpFS.
Follow this guide.
This guide explains how to install and configure a SSH server for a Windows XP home computer. SSH (Secure Shell) is a secure communications networking protocol based on the client-server model. It’s used to log into and execute commands between remote computers or devices and is widely used as a secure replacement for the insecure telnet and rlogin protocols. SSH encrypts all of the data, including the authentication data, allowing secure communications over unsecured networks, such as the Internet. Connections are made using public-key cryptography or password authentication, while the data itself is encrypted using one of several included encryption algorithms. It supports tunneling, port forwarding and transferring files with the associated protocols SFTP (Secure File Transfer Protocol) and SCP (Secure Copy Protocol), which are part of the standard SSH package. Typically used on Linux and UNIX systems, SSH runs on Windows systems using Linux-like environments such as Cygwin.
Benefits of SSH
- Enhanced Security – user and host authentication, data encryption and integrity
- Remotely connect computers (running Windows or Linux) and execute commands
- Use applications such as Filezilla or WinSCP for file management operations on the same computer or from a remote computer
- TCP/IP and X11 connection tunneling (a slightly more complex topic not explained in this guide)
Sshfs Windows 10 Bash
The OpenSSH package
This guide uses the free and precomplied version of the OpenSSH suite, a stand alone version of SSH using a stripped down version of Gygwin. This allows for a quicker and smaller installation than if OpenSSH is installed as part of a regular Cygwin installation. The OpenSSH suite consists of the SSH program, SCP, SFTP and several supporting utilities (see https://openssh.org). The Windows version of OpenSSH hasn’t been updated for sometime, so the latest pre-compiled version available for Windows is v3.8.1p1-1 (July 2004), which still works well. See https://sshwindows.sourceforge.net/ for more information. For this guide, the SSH server is setup for password authentication.
______________________________________________________________________________
Step 1: Install OpenSSH
- Download OpenSSH for Windows v3.8.1p1-1. This is the direct download link.
- Unzip the archive and then run the installer setupssh.exe.
- Change the installation location to “C:OpenSSH” instead of program files to avoid spaces in directory names.
- Use the default settings as shown on the screen-shot below.
- That’s it for the installation; however, the SSH server’s passwd file must be configured next before using.
Sshfs Windows 8.1 Command
OpenSSH installation options
Step2: Configure OpenSSH
- On your computer, click Start–> Run–> Type in “cmd” (without quotes), and then hit the OK button.
- In the command window, cd to the “OpenSSHbin” folder. If you are changing ports, go to the next step; otherwise, skip to Step 4.
- (Optional step) OpenSSH uses port 22 by default. If for some reason you need to use another port, you can change the port assignment for OpenSSH to prevent port conflicts. In the command window, cd to “OpenSSHetc” and enter “edit sshd_config” to launch the command line editor to change the port assignment (this is at approx line 13 in the file – an external text editor such as notepad may also be used). For example, to change the port to 5704:
#Port 22
change to:
Port 5704
(note that “#” needs to be removed to change the port assignment. Any other unused port other than 5704 is also OK)
Make sure to save the file - Enter the following in the command window. In the following commands, -l indicates local and -d indicates domain. Press Enter after each line; don’t include quotes:
- “mkgroup -l >> ..etcgroup”
- Creates a group file for local user accounts
- “mkgroup -d >> ..etcgroup” (skip – not normally required)
- Creates a group file for domain users. Returns [2453] if there is no PDC – primary domain controller
- Most instructions state to run both of the above commands. However, the “OpenSSHreadme.txt” file in “OpenSSHdoc” states: “If you use both mkgroup commands, the group file will contain duplicates. You will need to remove these by hand in a text editor.” Kind of confusing, but when both are executed I got the [2453] error for -d, but it didn’t change anything in the group file.
- “mkpasswd -l -u username >> ..etcpasswd”
- Adds a local authorized user to passwd file for local user accounts. NOTE: Omitting the username switch adds ALL users from the machine or domain, including service accounts and the Guest account.
- “mkpasswd -d -u >> ..etcpasswd” (skip – not normally required)
- Adds passwd file for all domain user accounts. Returns [2453] if there is no domain controller
- Again, if you get the [2453] error with the -d switch above, it doesn’t apply and won’t change anything in the passwd file.
- “mkgroup -l >> ..etcgroup”
- Enter net start opensshd to start the SSH server (net stop opensshd stops the SSH server). It’s installed as a service, so in the future, the server will automatically start each time the computer boots.
- The SSH server is now configured with password authentication (the default configuration). If you want to use public key authentication, you need to generate public and private keys using the supplied executable and change the sshd_config file. Note that the “keyauthentication.txt” file in the “OpenSSHdocs” directory states: “This document is outdated. You can use this as a reference, but please don’t expect it to be accurate. I will update this soon.” In any case, it shouldn’t be too difficult to accomplish public key authentication using the “keyauthentication.txt” by cross referencing its information with additional sources. Some other sources explaining how to setup public-key authentication for OpenSSH are below:
OpenSSH RSA Authentication for Windows and Linux
ssh-keygen Tutorial – Generating RSA and DSA keys
OpenSSH for Windows - Done with the configuration. Next, testing the SSH server.
Test the installation on the SSH server (from the same machine)
- Enter ipconfig in the command window to find your ip address.
- Enter ssh [email protected] or ssh [email protected] (servername = computername) into the command window to login using SSH. You can also use any of the login options listed at the end of this page for logging in using a command window on the PC with the SSH server.
Note: You may get a usage warning screen as shown below. If so, ignore it and sign in with your password. Also note that if you are logging in to the server for the first time, depending on the application being used to connect, you may also get another warning similar to: “The server’s host key was not found in the cache. You have no guarantee …blah blah… rsa2 key fingerprint is: ssh-rsa 1024 95:3c:9e:2b:23:df:bd:57:b4:ad:f1:5f:4c:2f:9c:ba “. This warning can also be safely ignored if you know the SSH server is the correct one you intended to log into. The warning is an anti-spoofing technique where each server is given a unique host key to prevent it from imitating another server. This technique is explained in detail on the WinSCP web site. - It’s working if you get the screen below. Next, some optional tweaking for changing the home directory.
SSH login warning screen
Optional Tweaking
Changing the Home Directory within Documents and Settings for user(s):
By default all user home directories are set to (/home/username) in the passwd file in the “OpenSSHetc” directory, where (/home) corresponds to “C:Documents and Settings” for Windows XP. This is somewhat inconvenient since most users may want to start in “My Documents”. To change it, open the passwd file in a text editor and change the second to last entry from “/home/username” to “/home/username/My Documents” and save. Entries are separated by a colon “:” for each user and are located just before the “/bin/switch” entry (switch stands for switch.exe, which enables both scp/sftp and the SSH standard command prompt to be available by switching between them).
Changing Home to outside the default directory on the SSH Server
To place users outside the default directory for their Windows profile, you need to change the directory that (/home) corresponds to by editing the value of the “native” key in the registry under (HKEY_LOCAL_MACHINESOFTWARECygnus SolutionsCygwinmounts v2/home). The value of “native” corresponds to the (/home) directory in the passwd file. For instance, if the “native” entry is changed to C:Users, then all users will be placed under separate folders in that directory — e.g., C:Usersusername1, C:Usersusername2, etc. If you then change each user (/home/username) in the passwd file to just (/home), this puts those users under C:Users. If you have a subdirectory such as “C:UsersOpenSSH”, you can place users there by changing the entries in the passwd file to (/home/OpenSSH) or (/home/OpenSSH/username) for separate user account directories.
Note that changing the home directory using this method works only for logins (Passwd), and doesn’t work for for SCP or SFTP. Instead, use Cygdrive Notation to change the directory for using Passwd, SCP, and SFTP (explained in next paragraph).
HKEY_LOCAL_MACHINESOFTWARECygnus SolutionsCygwinmounts v2/home
Changing the Drive of the Home Directory when using Passwd, SCP, and SFTP (Cygdrive Notation)
To access any folder on any drive letter outside the installation root (/home), a special notation called Cygdrive is required when using SCP, SFTP and for the home directory entries in passwd. Cygdrive notation changes the mapping of drive letters by mapping them into a UNIX-style file-system. Cygdrive notation overrides all other settings in the registry.
To use, add “/cygdrive/driveletter” to the start of the folder path in the user passwd file and/or when using the SCP or SFTP commands. For instance, to change to the “C:windowssystem” directory in a command window use: “cd /cygdrive/c/windows/system“. To transfer file example.txt to d:test using SCP, the command would be “scp example.txt [email protected]:/cygdrive/d/test/“.
You can even change the prefix of cygdrive notation by adding two entries to the registry. Open HKEY_LOCAL_MACHINESOFTWARECygnus SolutionsCygwinmounts v2, and add a REG_DWORD called “Cygdrive flags” and set it to 2a hex. Then add a REG_SZ called “Cygdrive prefix” and set its value to the new prefix. For instance, if you set it to “/” then the C: drive becomes accessible using Cygdrive notation “/c”, the D: drive with “/d”, or the F:test folder with “/f/test” and so forth. If it’s set to “/foo”, then the C: drive becomes accessible using Cygdrive notation “/foo/c”, the D: drive with “/foo/d”, or the F:test folder with “/foo/f/test” and so on. This behavior can be tested in a command window using the command “mount –change-cygdrive-prefix /foo” before permanently changing the registry.
______________________________________________________________________________
Remote connections from the network
To connect to the SSH server from a remote computer on the network, a SSH compliant client is needed. SSH is usually installed by default on Linux systems, and SSH clients such as Putty are often included as well. If the remote computer will be a Windows machine, it needs to have at least the Cygwin or OpenSSH client installed in order to connect with the SSH server from a command window, while Putty is a stand-alone application. The client portion for OpenSSH can be installed separately during the OpenSSH installation process. The installation process sets the path variable for the OpenSSH client and/or Server, so that SSH commands are available from any command window on that machine. Even with an OpenSSH or Cygwin client installed, it’s a good idea to have a client like Putty also installed, because it makes connecting much simpler.
Connecting from the outside world
To connect to the SSH server from the outside world, you need to port forward port 22 (or the port set during the OpenSSH installation) to the router. Port forwarding can be setup with a program like SimplePortForwarding or by following instructions in the router user’s manual. This sets up the router to forward any connection to port 22 to the SSH server. Then, all that’s needed to connect is to use a terminal in Linux, a command window in Windows, or a client like Putty from any computer connected to the Internet and the public IP address for your router.
Using Filezilla, WinSCP and Putty
Client utilities such as Filezilla, WinSCP, and Putty can be used on the computer with the SSH server, from remote computers on the LAN, and from the outside world to connect to the SSH server. When using any of these utilities from the SSH server machine, you can use 127.0.0.1, computername, or localhost as the IP with the user login and password info for those accounts. You can also use the SFTP protocol for Filezilla, SCP or SFTP for WinSCP, and SSH for Putty. The beauty of using WinSCP or Filezilla on an SSH server machine is that file tasks like changing permissions with CHMOD, moving, or deleting files are easily accomplished using a mouse and the application UI, such as those for locally installed web sites. In other words, unlike natively installed servers, such as a FTP server, the SSH server and applications using the server can run on the same machine without any loss of functionality since the SSH server runs in a separate environment (Cygwin) using the loopback interface.
Putty config screen (hostname can also be localhost or 127.0.0.1)
List of connecting options from command window and applications:
Using a Command Window:
Password will be the same as the user password for that machine (commands are case sensitive)
- On the SSH server:
- ssh [email protected]
- ssh [email protected]
- ssh [email protected]
- ssh [email protected]
- Remote computer on the network with SSH client installed:
- ssh [email protected]
- ssh [email protected]
- Remote computer from outside world with SSH client installed:
- ssh [email protected]:port (remote ip address for your router set with port forwarding)
Using client applications such as Putty, WinSCP or Filezilla
User Name and Password will be the same as the user login credentials for that machine
- On the SSH server:
- IP Address: 127.0.0.1, localhost, servername, or 192.168.x.xxx
- Remote computer on the network:
- IP Address: servername or 192.168.x.xxx
- Remote computer from outside world (router set with port forwarding):
- IP Address: xxx.xxx.x.xxx (remote ip address, port usually set in application)
______________________________________________________________________________
Sshfs Windows 8.1 App
Using SSH commands other than for connecting is another topic and not covered in this guide; however, a few are explained at the following:
Sshfs Windows Server
ezpz Hosting – Common SSH Commands – Linux Shell Commands
Sshfs Windows 8.1 Installer
The Geek Stuff – 5 Basic Linux SSH Client Commands
Taming the Beast – Using SSH and Unix commands – a beginners tutorial
____________________________________________________________________________
Unofficial OpenSSH Suite installer for Windows – mls-software.com (ver 6.6.1p1-3 tested on 10/08/2014 with Windows XP. Server requires several additional protocols and drivers. It also has a slightly different setup. Possibly could work, but not worth the investment in time and effort.)
If you have found a spelling error, please, notify us by selecting that text and pressing Ctrl+Enter.
